- Published on
Integrating Azure Active Directory with Windows Forms Application
- Authors

- Name
- Mohammed Rabby Hasan
- @rabbyalone
 Today we're gonna imlement Azure Active directory authentication in our Desktop windows forms app. Azure AD is one of the pioneer cloud based authenticaton provider. We will use OAuth protocol Azure AD to authenticate users into our windows forms application.
Today we're gonna imlement Azure Active directory authentication in our Desktop windows forms app. Azure AD is one of the pioneer cloud based authenticaton provider. We will use OAuth protocol Azure AD to authenticate users into our windows forms application.
Microsoft Entra ID (known as Azure AD) in brief
Microsoft Entra ID or previously Azure AD is Microsoft's cloud based identity and access management service which provides security services for employees and organization. It has capabilities including
- Single Sign On (SSO)
- Multi-factor Authentication
- Device Registration
- Access management
Protocols
- OAuth
- OpenID Connect
- SAML
Today we're gonna discuss implementation using OAuth to authenticate our windows forms application.
Let's Get Started..
Register the Application in Azure AD
-
Go To
portal.azure.comthen go to search forMicrosoft Entra IDpreviouslyAzure ADor Go to Microsoft Entra Admin center and login -
Browse to Identity > Applications > App registrations and select New
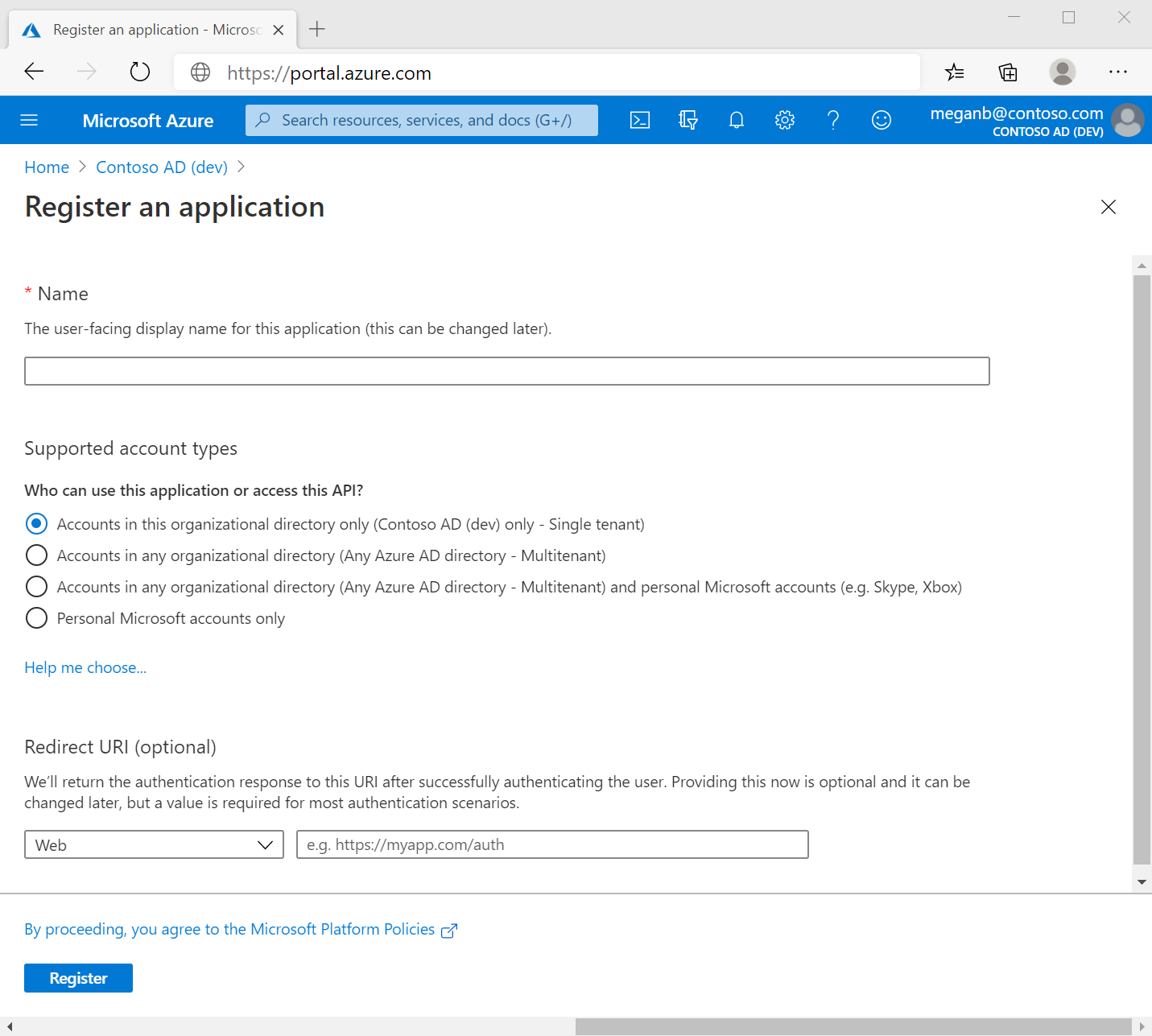
-
Choose your application access then next and save, After completing the app registrtion it will show you the overview
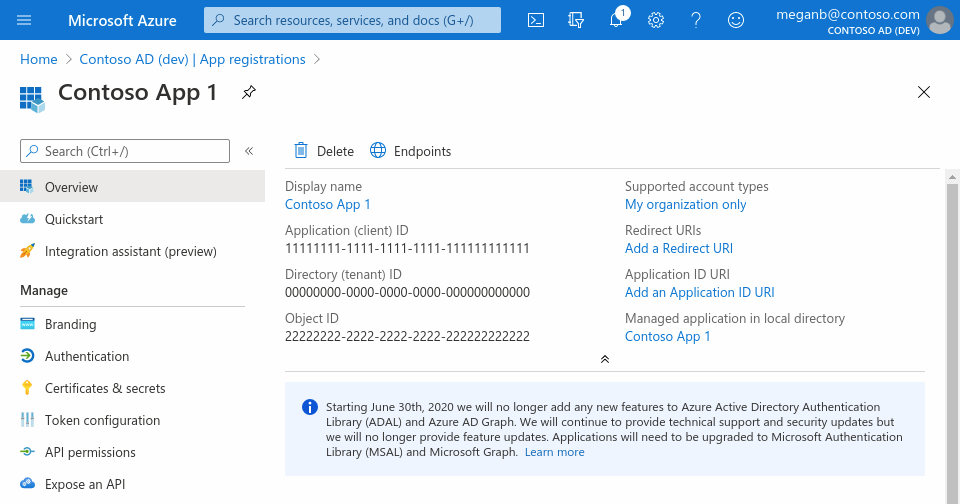
-
Setting up rediect uri by clicking add a Redirect URI. We will select this redirect URI
https://login.microsoftonline.com/common/oauth2/nativeclient
Read More at Microsoft Learn
Configure Authentication
we will create windows forms application and install this nuget library
Microsoft.Identity.Client
Get Access Token
- We will setup our clientID, TenentID an Scopes from appregistration page
string clientId = "copy from app registration overview";
string tenantId = "copy from app registration overview";
string[] scopes = new string[] { "User.Read" };
- Add sign in button to the form and write get accees token logics there
in the get access token method we need to fetch based on those options
PublicClientApplicationOptions options = new PublicClientApplicationOptions();
options.ClientId = clientId;
options.Instance = "https://login.microsoftonline.com/common";
options.RedirectUri = "https://login.microsoftonline.com/common/oauth2/nativeclient";
var app = PublicClientApplicationBuilder.CreateWithApplicationOptions(options)
.WithAuthority(AzureCloudInstance.None, tenantId)
.Build();
if app builds succesfully we can request for access token
var accounts = await app.GetAccountsAsync();
AuthenticationResult result;
try
{
result = await app.AcquireTokenSilent(scopes, accounts.FirstOrDefault())
.ExecuteAsync();
}
catch (MsalUiRequiredException)
{
try
{
var res =
Task.Factory.StartNew(async () => await app.AcquireTokenInteractive(scopes).ExecuteAsync());
result = res.Result.Result;
}
catch (MsalException ex)
{
Console.WriteLine(ex.Message);
throw;
}
}
- Once done your application looks like this
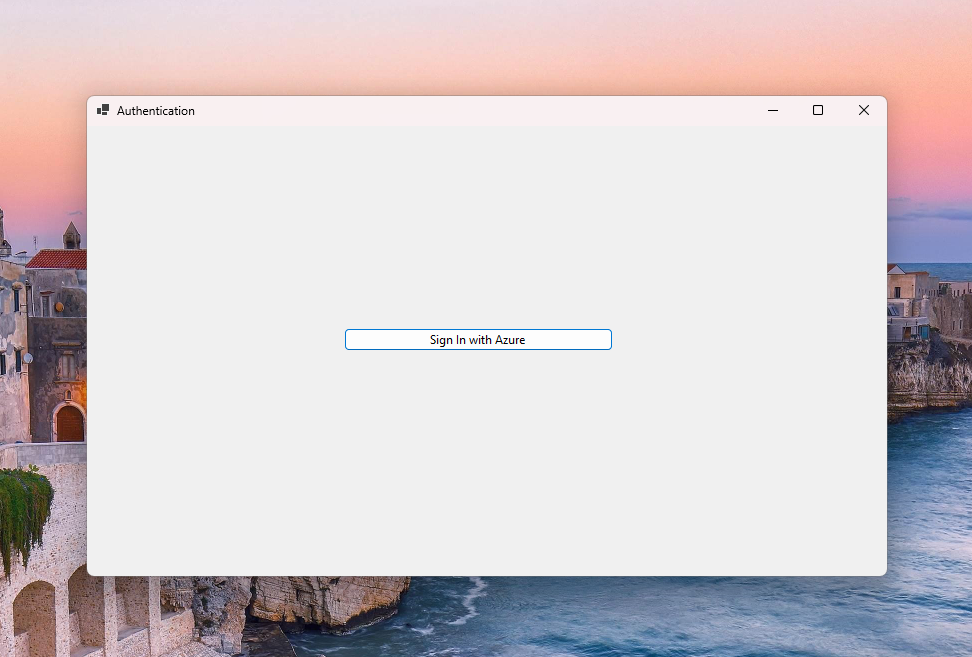
Prompt for user login using microsft login screen.
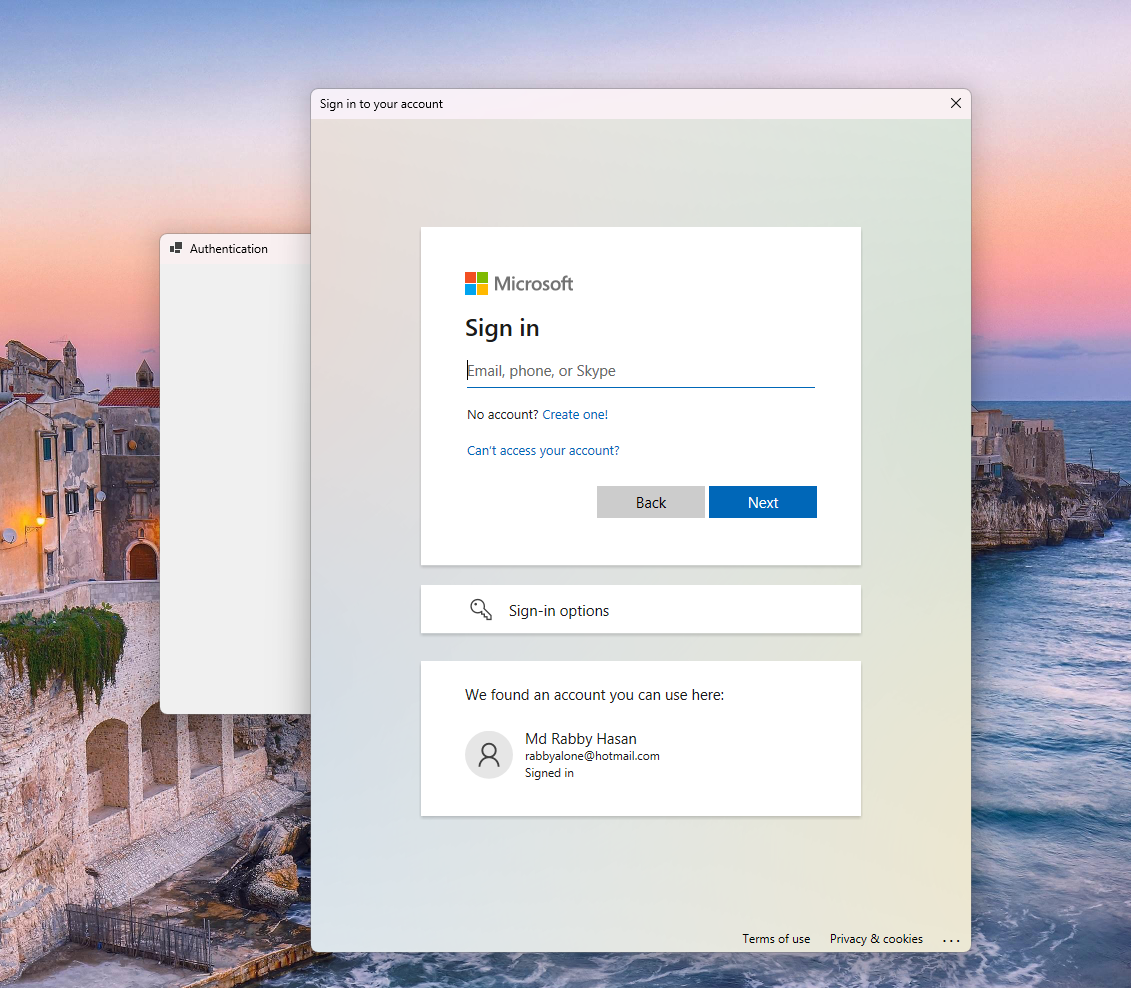
See full authentication class implemtation here
GitHub repository for the full implementation https://github.com/rabbyalone/TriangleApp